Open access, read now

Thanks to the support Concordia University's Open Access Fund and the University of Minnesota Press, Internet Daemons is open access through Manifold and as a PDF through Concordia's Spectrum library.
Read the bookWe’re used to talking about how tech giants like Google, Facebook, and Amazon rule the internet, but what about daemons? Ubiquitous programs that have colonized the Net’s infrastructure—as well as the devices we use to access it—daemons are little known. Fenwick McKelvey weaves together history, theory, and policy to give a full account of where daemons come from and how they influence our lives—including their role in hot-button issues like network neutrality.
Going back to Victorian times and the popular thought experiment Maxwell’s Demon, McKelvey charts how daemons evolved from concept to reality, eventually blossoming into the pandaemonium of code-based creatures that today orchestrates our internet. Digging into real-life examples like sluggish connection speeds, Comcast’s efforts to control peer-to-peer networking, and Pirate Bay’s attempts to elude daemonic control (and skirt copyright), McKelvey shows how daemons have been central to the internet, greatly influencing everyday users.
Internet Daemons asks important questions about how much control is being handed over to these automated, autonomous programs, and the consequences for transparency and oversight.
Beneath social media, beneath search, Internet Daemons reveals another layer of algorithms: deeper, burrowed into information networks. Fenwick McKelvey is the best kind of intellectual spelunker, taking us deep into the infrastructure and shining his light on these obscure but vital mechanisms. What he has delivered is a precise and provocative rethinking of how to conceive of power in and among networks." —Tarleton Gillespie, author of Custodians of the Internet
"Internet Daemons is an original and important contribution to the field of digital media studies. Fenwick McKelvey extensively maps and analyzes how daemons influence data exchanges across Internet infrastructures. This study insightfully demonstrates how daemons are transformative entities that enable particular ways of transferring information and connecting up communication, with significant social and political consequences." —Jennifer Gabrys, author of Program Earth

Oliver Selfridge, a seminal thinker in machine learning, imagined computer programs as a world of demons. The introduction extends this metaphor to imagine another artificial intelligence, the internet. Its distributed operations relies on daemons -- programs running in the internet infrastructure -- to manage information flows. Daemons have begun to more actively manage these flows as they have become more intelligent, a matter of active regulatory concern and closely related to network neutrality.

From heat engines to the military-academic-industrial complex, the first chapter follows the legacy of Maxwell’s Demon. The thought experiment of James Maxwell bedeviled many researchers integral to the origins of digital communication and control. By following this demon through the beginnings of computers, networking and control, this chapter explore how an imaginary demon inspired real internet daemons. For scholars in communication and media studies, the chapter also makes a new link between the cyborg sciences and the origins of digital communication.

Deep in the heart of the American military-academic-industrial complex, researchers at the Advanced Research Projects Agency drew together cutting-edge research to build an experimental ‘packet-switched’ computer network, the ARPANET. For it to work, computers had to be part of its infrastructure. Known as Interface Message Processor or IMPs, these military-grade computers built the ARPANET and hosted the first Internet daemons. They faced an intractable problem, how to optimally run a multimedia medium. Adding to histories of the Internet, this chapter highlights the enduring significance of this optimization problem and daemon’s various solutions.
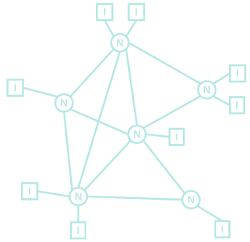
Daemons flourished as the ARPANET became one of many packet-switched computer systems. This chapter looks to the changing diagrams that found new places for daemons. As hosts, gateways and in between, daemons could be found everywhere in this emerging patchwork of networks that became the Internet. The optimization problem grew along with daemons with all kinds of new networks beyond time-sharing and real-time. As these networks converged into one Internet, daemons had to sort out the conflicting demands placed on the common infrastructure.

Step into any data center and hear the full roar of daemons today. Daemons run on servers distributed across the globe, housed in secure, secretive and mundane buildings. Together, these daemons connected the world in one digital communication system. This chapter describes the daemons working online to inspect, route and queue packets as well as coordinate themselves. After describing it's processes, the chapter travel through an Internet Service Providers operations and it's attempt to manage peer-to-peer networking over its cables. This journey reveals happening all through the core of the internet, between daemons abiding by their simple roles and a new class of intelligent programs conducting traffic under a new, more managed optimization.

How do we suffer from buffering? What is the labour of lag? Does disconnection cause distress? This chapter connects daemons to the experiences of being delayed online and the cultural stigmas that code these feelings of waiting and slowness. Conceptually, the chapter links the material affects of flow control with the feelings expressed through advertisements, designed by Internet Service Providers to capitalize on their power over this control. In the end, the chapter wonders if there is any dignity in being delayed together, a sentiment that might undercut daemons’ influence.
The Pirate Bay has been the homepage of Internet Piracy for over 15 years. The pro-piracy, anti-copyright groups has antagonized daemons as well as copyright holders. This chapter explores the strategies and tactics developed by TPB admins to elude daemons such as peer-to-peer file sharing and, more recently, a virtual private network (VPN) designed to cloak users’ traffic from watchful daemons. For readers interested in hackers, darknets and peer-to-peer, this chapter helps explain how these alternative networks struggle with daemons deep within the Internet’s infrastructure, largely outside public view.

Canadians had a hard time playing World of Warcraft in 2010. The massive multiplayer game was at the height of its popularity. But lag, disconnections and difficulty joining a game plagued gamers from sea to sea. These complaints led to a two-year inquiry by Canada’s media regulator into the traffic management practices, leading to one of the first applications of network neutrality policy. This two-year struggle to presents a critical case of daemonic media policy. As governments around the world struggle to hold algorithms accountable, this chapter explores the challenges to render the collective work daemons public, accountable and ultimately, responsible for their flow control.
The conclusion return to one lingering question. What of the UNIX purist who complains that the daemon is a term best reserved for operating systems alone? Shouldn’t the term daemon be reserved for programs managing printer queues? To this hypothetical objection, the chapter expanded the book’s vision of daemons to imagine them as part of vast, global operating systems controlled by Google, Apple, Facebook, Amazon and Microsoft. The final chapter applies the book’s daemonic media studies to explore howf control might work in these operating systems.
You can buy Internet Daemons this Fall from the University of Minnesota Press or Amazon.
Buy Internet DaemonsDr. McKelvey is an Associate Professor in Information and Communication Technology Policy in the Department of Communication Studies at Concordia University. He studies the digital politics and policy, appearing frequently as an expert commentator in the media and intervening in media regulatory hearings. He is co-author of The Permanent Campaign: New Media, New Politics (Peter Lang, 2012) with Greg Elmer and Ganaele Langlois. His research has been published in journals including New Media and Society, the International Journal of Communication, public outlets such as The Conversation and Policy Options, and been reported by The Globe and Mail, CBC The Weekly and CBC The National. He is also a member of the Educational Review Committee of the Walrus Magazine.